Throughout the month of October, we have taken a close look at the Cybersecurity and Cyberthreat landscape, and discovered some of the main vectors in cyberattacks, including Phishing, Ransomware, and DDoS attacks.
Not only the threat of said attacks is increasing, however, but so is the financial impact they have on their victims. The global average cost of a data breach, according to IBM’s most recent Cost of a Data Breach Report reached $4.45 million in 2023, constituting an increase of $100.000 compared to the previous year ($4.35 million in 2022).
Of the data breaches in question, 82% involved data stored in cloud environments, making them a popular target for cyberattacks in 2023. With attackers gaining access to multiple cloud environments in 39% of cases, the cost of breaches targeting the latter was higher than average, at $4.75 million.
Taking into account that a cyberattack often results in a number of costs such as the expenses necessary to mitigate them, and more immediate financial consequences such as business losses, this amount is divided into four cost segments:
.png?width=451&height=291&name=Screenshot%20(68).png)
Measured in USD millions
Source: IBM Cost of a Data Breach Report 2023
Consequently, data breaches often result in organisations increasing the price of services or products, passing on the costs suffered from the attack to their consumers, which can immensely compromise a company’s market positioning and value perceived by its clients, potentially leading to customer backlash, loss of business, damage of reputation, and a competitive disadvantage.
Meanwhile, cost savings of $1.49 million have been achieved by organizations that invested in high level IR (Incident Response) planning and testing. An average of $232,867 were saved by employee training, $232,008 by IR plan and testing, and $221,794 by having a dedicated IR team.
Cyber-resilience is an organisation's capacity to prevent, resist, and recover from cybersecurity incidents.
An important aspect when considering the importance of employee training and internal defence systems in relation to the cost of a data breach is its lifecycle. When a cyberattack is successfully identified by internal teams or tools it takes approximately 28.2% less time to contain the data breach than when it is disclosed by the attacker, and can cost organisations up to $1 million less. In 2023, 27% of data breaches were disclosed by the perpetrator as part of a ransomware attack. They took a mean time of 320 days to identify and contain, and cost organisations an average of $5.23 million, whereas internally detected attacks took 241 days, and cost an average of $4.30 million (-19.5%).
Furthermore, employee training decreases the potential of human error as a vessel for cyberattacks.
Considering “Cybercrime would be the world’s third largest economy after the U.S and China, if measured as a country,” as stated by Cybercrime Magazine, it is important to address what we can in order to confront it, including, and especially, the human element, which was involved in 82% of data breaches in 2022.
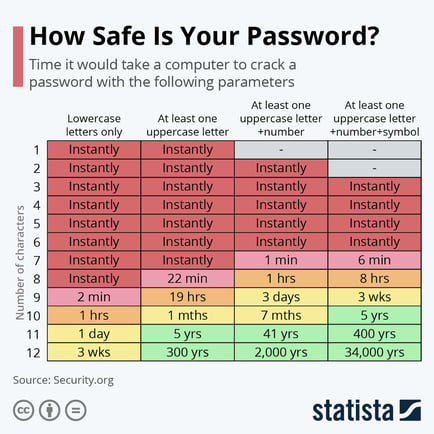
An alarming number of data breaches is attributed to compromised passwords. As one of the less complex elements of good cybersecurity practices, this is an issue that demands little effort to be rectified.
The longer and more complex a password is, the longer it takes for a hacker to be capable of cracking it.
In addition, 61% of organisations globally have implemented a zero-trust initiative in 2023, as apposed to 24% in 2021. The Zero Trust strategy is a concept which combines a set of cybersecurity principals to improve network security and strengthen an organisation’s security posture to protect it from threats, assuming the latter can originate from both external and internal sources. The notion behind it: “Never trust, always verify.”
Naturally, this involves educating employees about safe practices, but also diminishes the potential of human error through the implementation of key principals such as:
- MFA (Multi-Factor Authentication) and IAM (Identity and Access Management), to securely verify a user’s identity, before granting access to the network or specific resources
- Least privilege access, to reduce the attack surface, by giving users and devices the minimum level of access necessary to perform their tasks
- Monitoring, to efficiently identify and respond to potential threats, by continuously tracking and analysing network traffic and user behaviour, which may indicate unusual or suspicious activity
- Micro-segmentation, to prevent lateral movement by attackers who may have already gained access, by creating segments to isolate and compartmentalise different parts of the network
- Encryption, to protect data from eavesdropping and tampering.
The investment in extensive security AI and automation has also proven to dramatically reduce the costs suffered by organisations as a result of a data breach, and minimise the time it took to identify and contain them. A difference of $1.76 million and 108 days was reported by said organisations, compared to those that did not use security AI and automation capabilities.
In the battle against cybercrime, the struggle for the upper hand may be perpetual, but will most certainly not be lost. The increasing sophistication of cybercriminal tactics is met with the consistent development of state-of-the-art technology, refined defence strategies, and robust security measures by collaborating nations, law enforcement agencies, and cybersecurity experts, further fortifying our collective defence against the evolving threat. In a collective effort to secure our advantage, we must remain alert in order to safeguard the integrity of our digital world and the data it contains. Information, education, and awareness play a vital role in creating and maintaining an online environment that is safe and reliable.
Helpful addresses:
Employee training:
FR: https://www.ssi.gouv.fr/administration/formations/
US: https://www.cisa.gov/cybersecurity-training-exercises
UK: https://www.ncsc.gov.uk/information/certified-training
Report cybercrime:
FR: https://www.internet-signalement.gouv.fr/PharosS1/ , https://www.service-public.fr/particuliers/vosdroits/N31138
US: reportphishing@apwg.org , https://reportfraud.ftc.gov/#/ , https://www.ic3.gov/
UK: report@phishing.gov.uk , https://www.asa.org.uk/make-a-complaint.html
EU: phishing@eui.eu , https://www.eui.eu/Helpdesk , https://fns.olaf.europa.eu/ , https://www.europol.europa.eu/report-a-crime/report-cybercrime-online
Sources: IBM , Techopedia, CSO