Cybersecurity Awareness Month: Phishing
Cybersecurity | Phishing | Awareness

In 2013, numerous employees in the accounting departments of Google and Facebook began receiving emails containing invoices and contracts signed by executives and agents of their respective companies from their Taiwanese infrastructure supplier Quanta Computers. Over the course of the following 24 months, the employees paid the multimillion dollar invoices, without so much as a second thought, before the suspicion of a phishing attack arose.
At this point, over $100 million had been transferred to a bank account belonging to the fake company of Lithuanian scammer Evaldas Rimasauskas, who, along with his co-conspirators, had spent the last two years creating false Quanta email accounts and carefully crafting the phishing emails, as well as forged letters, contracts, and invoices, subsequently laundering the money received through banks in Latvia, Cyprus, Slovakia, Lithuania, Hungary, and Hong Kong. After Google and Facebook took legal action upon eventually discovering the scam, Rimasauskas was arrested and extradited from Lithuania, before being sentenced to five years in prison in December of 2019.
Phishing: The use of unsolicited email, text messages, and phone calls purportedly from a legitimate source requesting personal, financial and/or login credentials.
While phishing is a notorious tactic that has been exploited long enough for it to seem like we should know better, it persists to be a popular and, above all, effective strategy to gain unauthorised access to sensitive data and funds, as its various forms have become increasingly sophisticated, and its effectiveness relies on the arguably weakest link in the security chain – the human element.
With approximately 3.4 billion phishing emails being sent every day, phishing attacks remain the most common form of cybercrime, as they serve not only as stand-alone attacks, but are often the entry point to launch more serious security threats, making them responsible for 90 % of data breaches worldwide.
The purpose of phishing is to gain access to sensitive data, steal login credentials, conduct identity theft, commit financial fraud, access corporate data and trade secrets, and obtain funds. To effectively execute the [mentioned], cybercriminals have developed numerous methods of phishing, the most common of which we have decided to highlight:
Email phishing
In the most prevalent form of phishing, attackers pose as a legitimate and trustworthy entity, such as a bank, social media platform, or courier service, in an email containing a link towards malicious attachments, or a fraudulent website requesting information like login credentials.
The most impersonated company in brand phishing attempts as of Q2 2023 is Microsoft, relating to 29% of all phishing attacks globally, followed by Google (19.5%), Apple (5.2%), and the following:
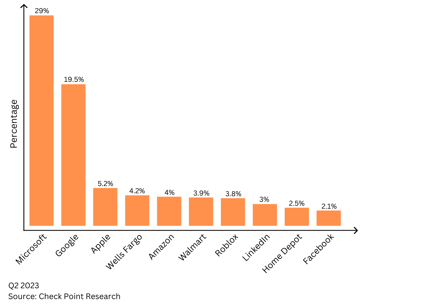
Despite various channels including SMS (Smishing) and phone calls (Vishing) being used in phishing attempts, email remains the predominant and most frequently exploited medium in the majority of phishing attacks.
Spear phishing
This type of phishing consists of emails customised for a specific individual or organisation, in which attackers impersonate a trusted individual or highly legitimate source, such as a relative or your boss. By gathering personal information about their target to make the phishing emails appear more convincing, they hope to obtain sensitive information – addresses, bank details, login credentials, etc. Within one year, approximately 88% of organisations encounter at least one spear phishing attack.
Clone phishing
Attackers replicate, or clone, a legitimate email containing a link or attachment, likely one that the target has received previously. They then slightly modify details in the email to include malicious links or attachments. To make the email appear to be from the same source as the first one, the perpetrator might replace small details in the sender’s address, for example change support@brand.com with supp0rt@brand.com, or use email subjects like: “Follow up on important information”, often including the target’s name.
Pharming
In pharming attacks, cybercriminals compromise DNS (Domain Name System) servers or manipulate host filed on victims’ devices, utilising malicious code and software, to reroute their web traffic to unsecure websites, in order to steal the target’s information. Websites you have visited before may suddenly look suspicious. Look out for different fonts, spelling errors, URLs beginning with http, rather than https, or error messages, such as “your connection is not private”!
Pop up
This type of attack leverages deceptive pop-up windows or dialogue boxes, often including false virus alerts by seemingly legitimate brands, in order to trick users into downloading malware onto their devices.
BEC (Business email compromise)
Due to the increase of remote work, there has been a notable rise in BEC attacks, which are a spear phishing tactic designed specifically to obtain confidential company information or making unauthorised money transfers, by impersonating a high-ranking executive or employee within the organisation.
As cybercriminals continue to refine their tactics, threats are becoming increasingly difficult to detect. Though putting in place robust security systems and software can prevent a significant number of cybercriminal activity from being successfully executed, responsibility still lies with the user to maintain vigilance in their online behaviour.
Education and awareness are key to remaining proactive, helping individuals recognise and resist phishing attempts, and allowing us to collectively work towards a safer online environment.
Sources: IC3 Report 2022 , IT Governance , Check Point Research, Cisco , Techopedia , Norton